In this guide, we will show you the steps to pass the “Meets Device Integrity” and Meets Basic Integrity” tests on your rooted device via the Play Integrity Fix module. Gaining administrative privileges by rooting your device via Magisk opens the floodgates to a plethora of customizations. But on the flip side, it does pave the way for the entry of a few issues as well, the primary among which is the tripping of SafetyNet.
Once that happens, you wouldn’t be able to use banking and payments, and even the likes of Uber and McDonald’s! So to rectify it, we already have got ourselves covered with a comprehensive guide on how you could pass the SafetyNet Test. After carrying out all the steps listed there, you’ll be able to easily use all the aforementioned listed apps. So this then begs an important question- why is there a need to pass the “Meets Device Integrity” and Meets Basic Integrity” tests? Let’s find out.
Table of Contents
What is Play Integrity?
Play Integrity is an API that is used by numerous applications to determine the device’s compatibility and security state. At the time of writing, many apps still use the SafetyTest, but many apps are ditching this tool and moving towards Play Integrity, with January 2025 being the deadline set by Google.
Once that time frame is reached and apps haven’t yet adopted Play Integrity, then there wouldn’t be any impact on your side [infact you will be the beneficiary as apps wouldn’t be able to check if your device is rooted or not, hence you’ll be able to use banking apps even on a rooted device!].
What is the Difference between Play Integrity and SafetyTest
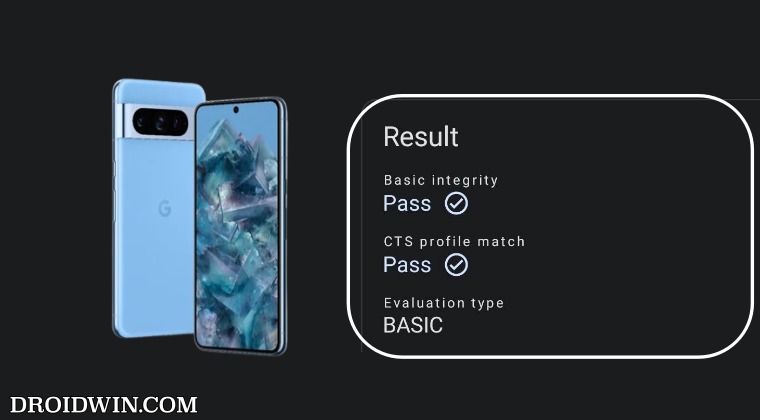
Most of the underlying aspects of both the Play Integrity and SafetyNet are near about similar, it’s just the responses that have been made a bit simpler in the former. But the major differences arise in the types of tests being conducted and more importantly, the results that you would be obtaining. As far as the SafetyNet tests are concerned, there exists the Basic Integrity and CTS Profile Match, and your device should pass both of these tests.
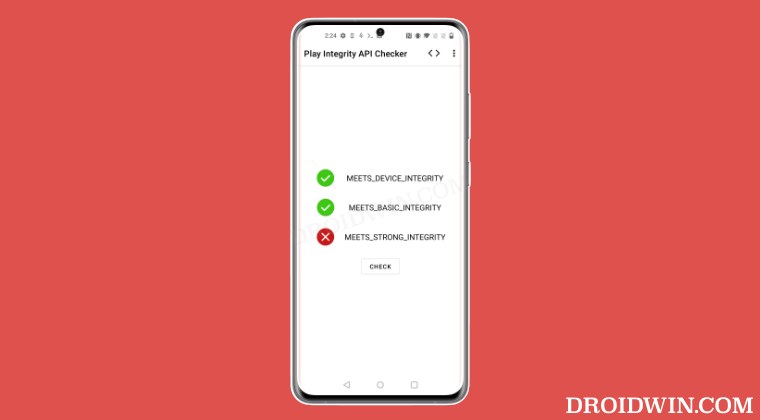
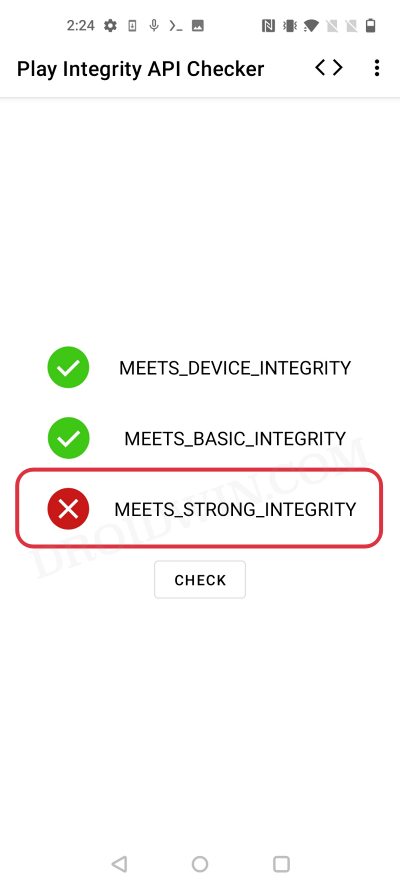
However, things aren’t the same on the other side of the fence. In Play Integrity, there are three tests performed- MEETS_DEVICE_INTEGRITY, MEETS_BASIC_INTEGRITY, and MEETS_STRONG_INTEGRITY, out of which your device should pass the MEETS_DEVICE_INTEGRITY and MEETS_BASIC_INTEGRITY. But why not the Strong Integrity?
Well, your device will not be able to pass the MEETS_STRONG_INTEGRITY until and unless the device’s bootloader is locked. Since that is not a possibility [because you cannot lock the bootloader on a rooted device], this test will always fail on your rooted device. However, do note that this wouldn’t conflict with your ability to use banking and payment apps on rooted devices as they only require you to pass the “Meets Device Integrity” and Meets Basic Integrity” tests.
How to Pass ‘Meets Device and Basic Integrity’ Tests
Let’s now get started with the most important part of this guide- the steps to pass the “Meets Device Integrity” and Meets Basic Integrity” tests on your rooted device. Before starting, please take a backup of all the data on your device, just to be on the safer side. Droidwin and its members wouldn’t be held responsible in case of a thermonuclear war, your alarm doesn’t wake you up, or if anything happens to your device and data by performing the below steps.
NOTE: Apart from failing in the rooted stock ROM, the Play Integrity might also fail if you are using a non-rooted Custom ROM. In that case, you will first have to root your custom ROM and then proceed with the below steps. While rooting might create some additional issues with banking apps, but we will deal with that later on in this guide, let’s first pass the Play Integrity Test. So root your ROM and only then proceed with the below steps.
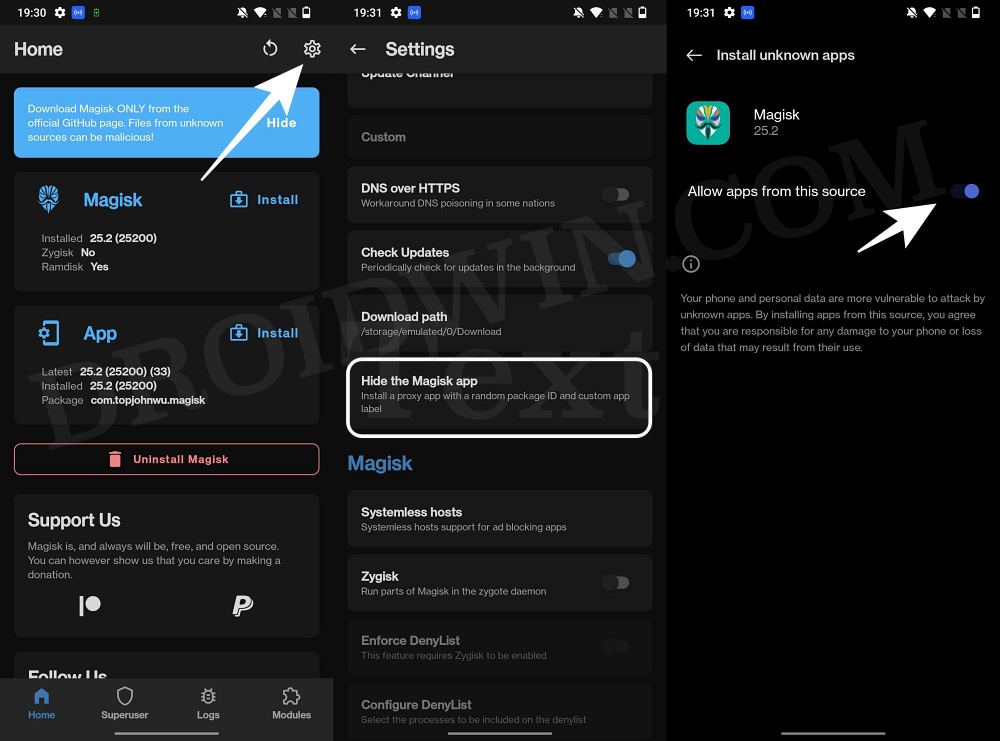
- Launch the Magisk App and tap on the settings icon situated at the top right.
- Then tap on Hide the Magisk App > Enable the toggle next to Allow apps from this source.

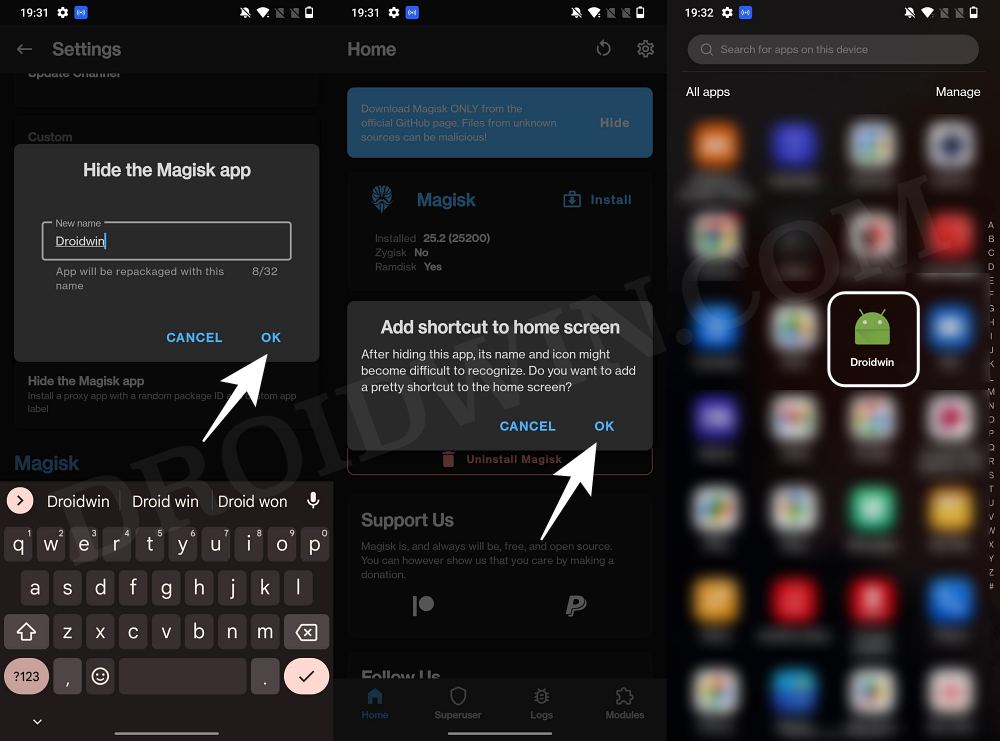
- Assign a new random name to this Magisk app and hit OK.
- It will now ask for a home-screen shortcut, tap OK [recommended].

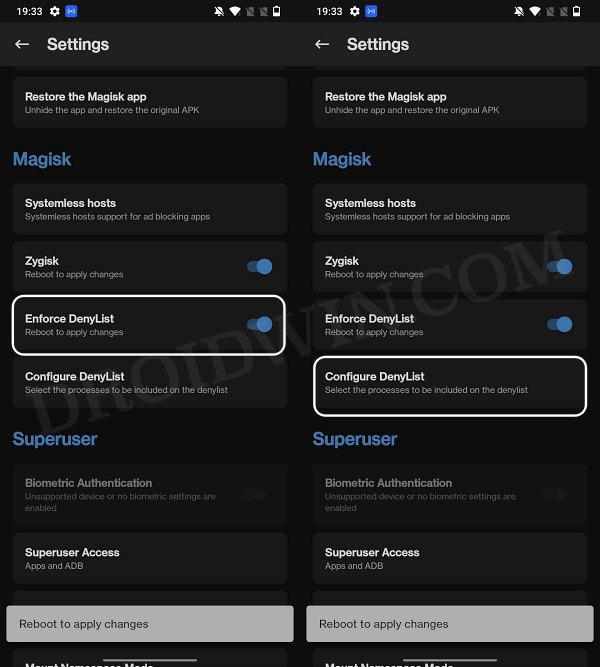
- Then enable the toggle next to Enforce Denylist. Now tap on Configure Denylist.

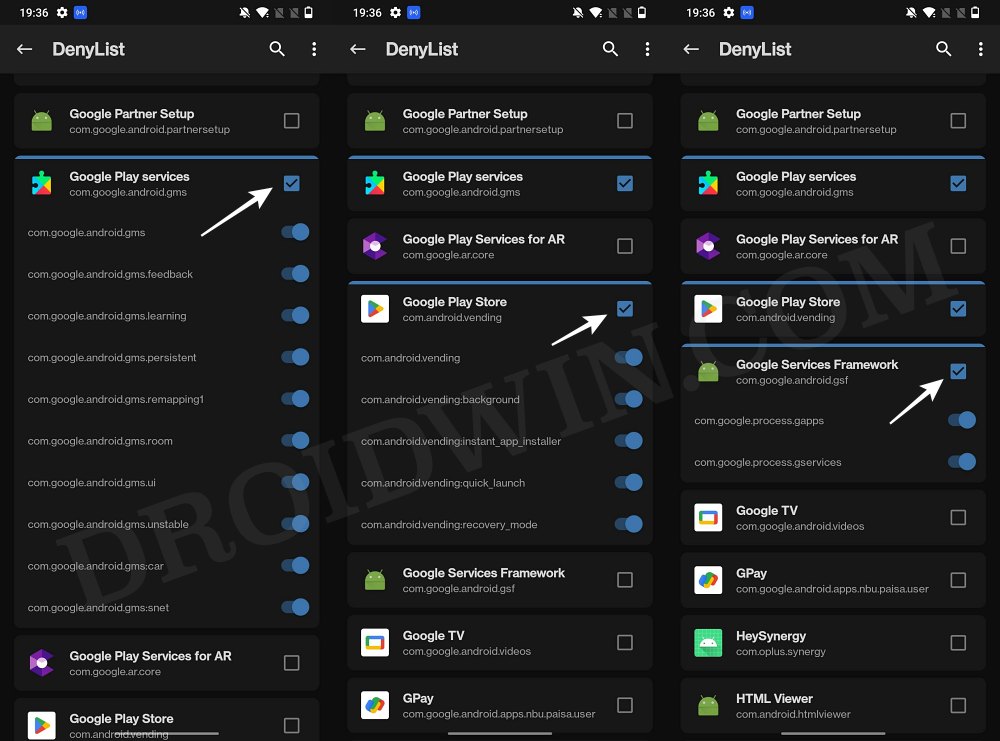
- Then expand the following apps and checkmark all its services
Google Play Service Google Play Store Google Service Framework Google Play Protect Service [if present]

- Likewise, do the same for the banking/payment apps of your choice.
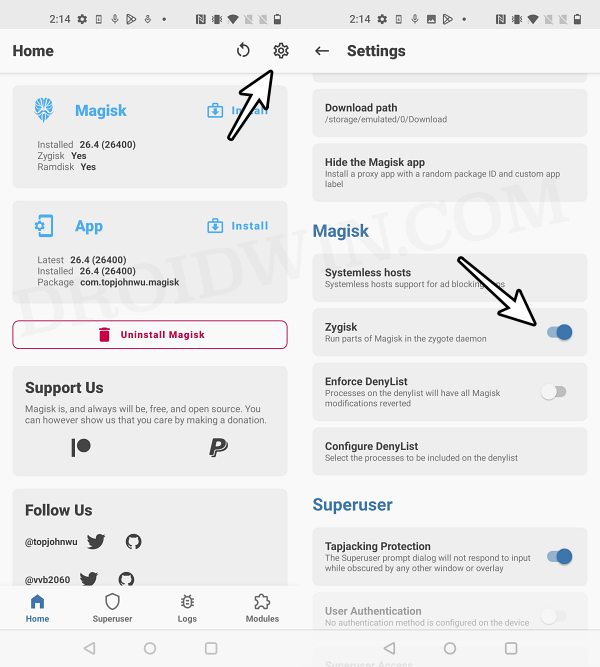
- Once done, again go to Magisk’s settings menu and enable Zygisk.

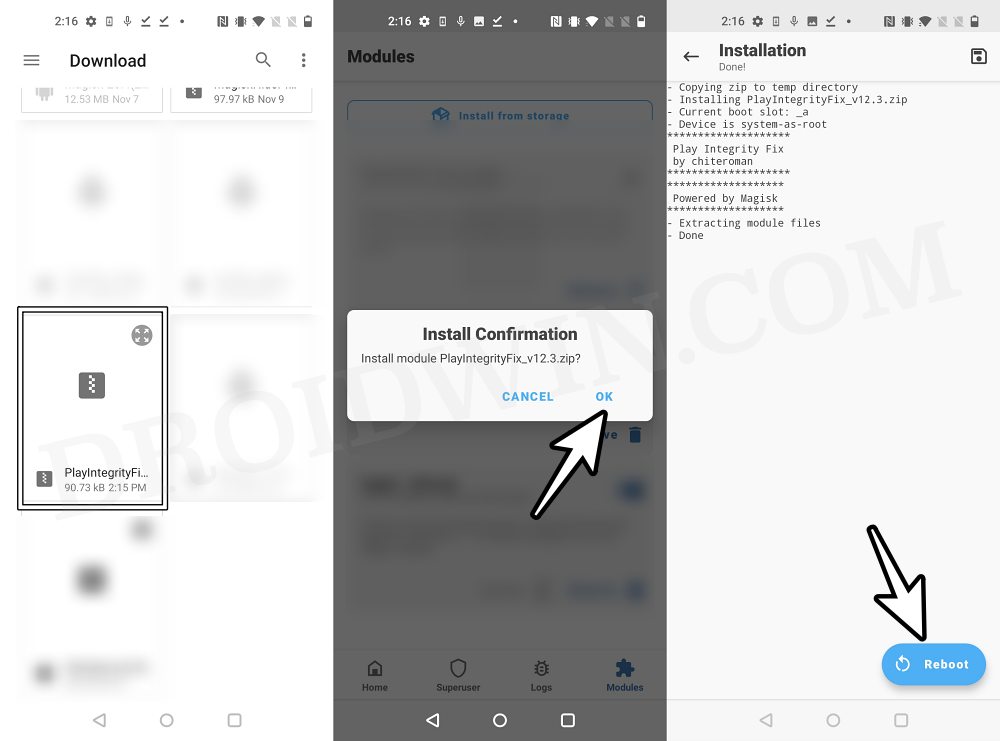
- Now download the “latest version” [extremely important] of the Play Integrity Fix Module from GitHub.
- Then flash the module via Magisk and restart your device.

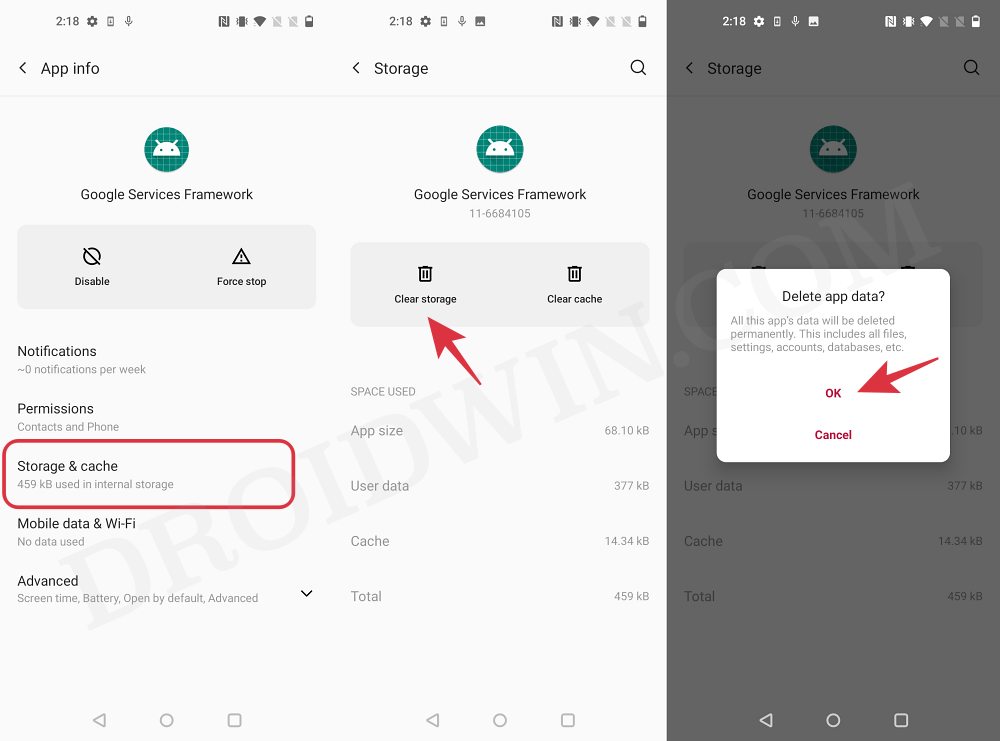
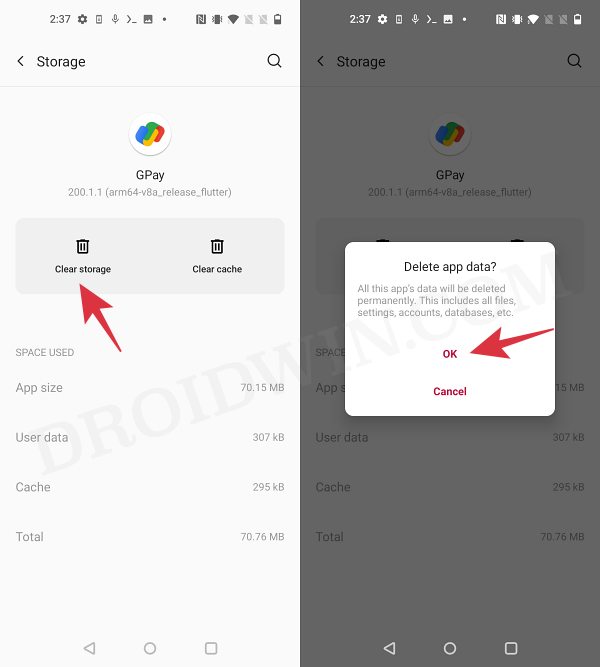
- Now delete the data of the Google Services Framework, Play Store, Play Service, and Play Protect Service [if present].

- Finally, delete the data of the banking/payment app of your choice.

- Once done, restart your device [compulsory] and then check out the result.
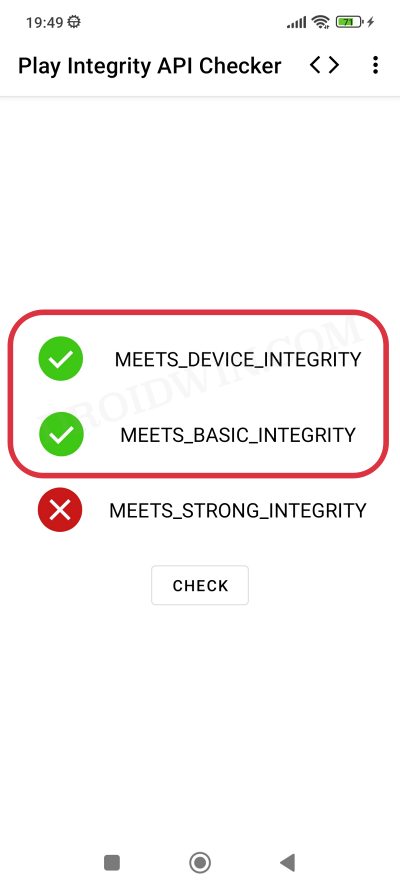
That’s it. Your rooted device should now pass both the “Meets Device Integrity” and Meets Basic Integrity” tests and you may verify the same via the steps given below. If you are still failing the test, then it means that the custom fingerprint that the module is using has been patched by Google. In that case, you should head over to our next section below. [Credits for this module: XDA Senior Member chiteroman].:
Using Custom Fingerprints/Build.Prop JSON File to Pass Play Integrity
Google has picked up the pace and is quickly patching the fingerprints for many devices. While the developer is doing his best to update his module with a newer one, but there doesn’t seem to be any end to this cat-and-mouse game the module is also open source, so Google is able to easily view the fingerprint that is being used and it ends up patching it!].
Use Custom Fingerprint/Build.Prop to Pass Play Integrity Test
If you pick up a less popular & old device’s fingerprint and create a custom JSON file, you could then easily pass the Play Integrity test, though it requires a few hit-and-trial approaches, but it will be worthy of an effort. Moreover, if you take this approach, then the chances of Google patching that fingerprint are quite low. So if the aforementioned module isn’t giving out the desired results, then you may try out our above guide and create your own fingerprint.
How to Pass Play Integrity on Rooted Android Without PC!
Thanks to a new fork of the Play Integrity module by Chiteroman, you might be able to pass the Play Integrity Test even without using a PC, just via a single APK file! You just have to launch the app once and it will auto-generate a new fingerprint, implement it onto your device, and delete the data of GMS. Once that happens, you have to restart your device and check if you pass this test [explained in the next section].
If you don’t, then simply relaunch the app- it will again generate a new fingerprint and implement it on your device. You’ll have to keep on doing so until you can pass the test. So with that in mind, here’s how to use this app:
Via FP Downloader
- To begin with, enable Zygisk from the Magisk’s settings menu.
- Then download the playcurl.zip and Play Integrity Fix modules.
- After that, launch Magisk, go to Modules, and tap on Install from Storage.
- Now select the playcurl.zip mod and hit OK in the confirmation prompt.

- The module will be flashed. Now flash the Play Integrity Fix module.
- Once done, restart your device. Now, go to Settings > Apps > See All Apps.
- Then select Fp Downloader > Notifications and enable all the notifications.
- Now launch Fp Downloader and you’ll get a Magisk prompt, tap on Grant.

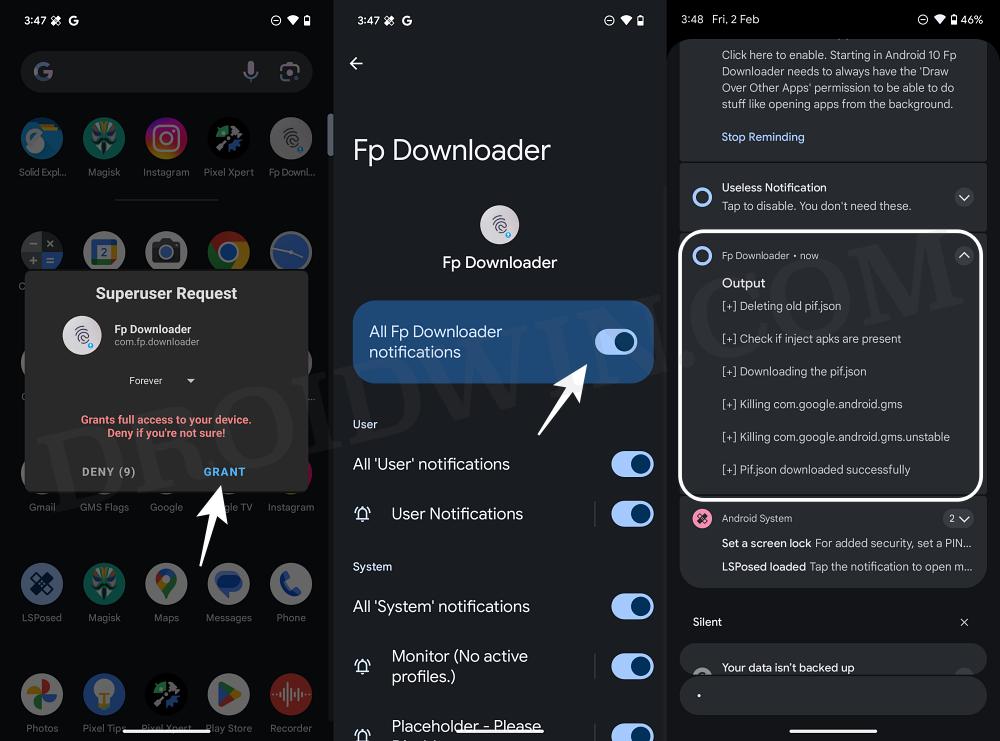
- Likewise, you’ll also get a notification that the new pif.json is implemented.
- Once that happens, check if your device is passing the Play Integrity or not.
- If it isn’t, then once again open the Fp Downloader and check out the result.
Note: You may also launch the app via a slightly more technical method, i.e. using Terminal. Here’s how:
- Download and install the Termux app from the Play Store.
- Then type in the below command and hit Grant in the SuperUser request.
su
- Now just type in the below command to invoke the module.
fp

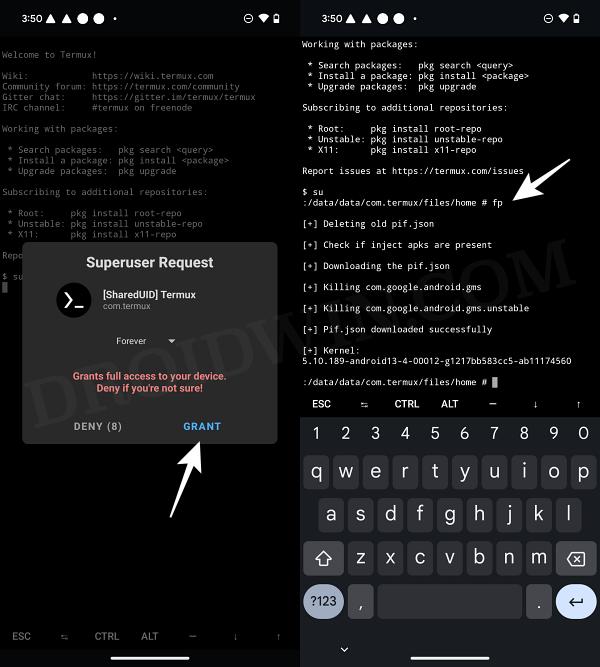
- The module will now run and change the device’s fingerprint.
- Once that happens, check if you are passing the test or not.
- If you’re not, then again type in fp. Do so until you pass the test.
Via AutoPIF-Next
It also works on the same principle as the aforementioned one. When the Fingerprint is banned, you will only need to open the AutoPIF app and then check for Play Integrity Attestation, the app will download the new PIF.json on /data/adb/pif.json.
- To begin with, enable Zygisk from the Magisk’s settings menu.
- Then download the playcurl.zip and Play Integrity Fix modules.
- After that, launch Magisk, go to Modules, and tap on Install from Storage.
- Now select the playcurl.zip mod and hit OK in the confirmation prompt.


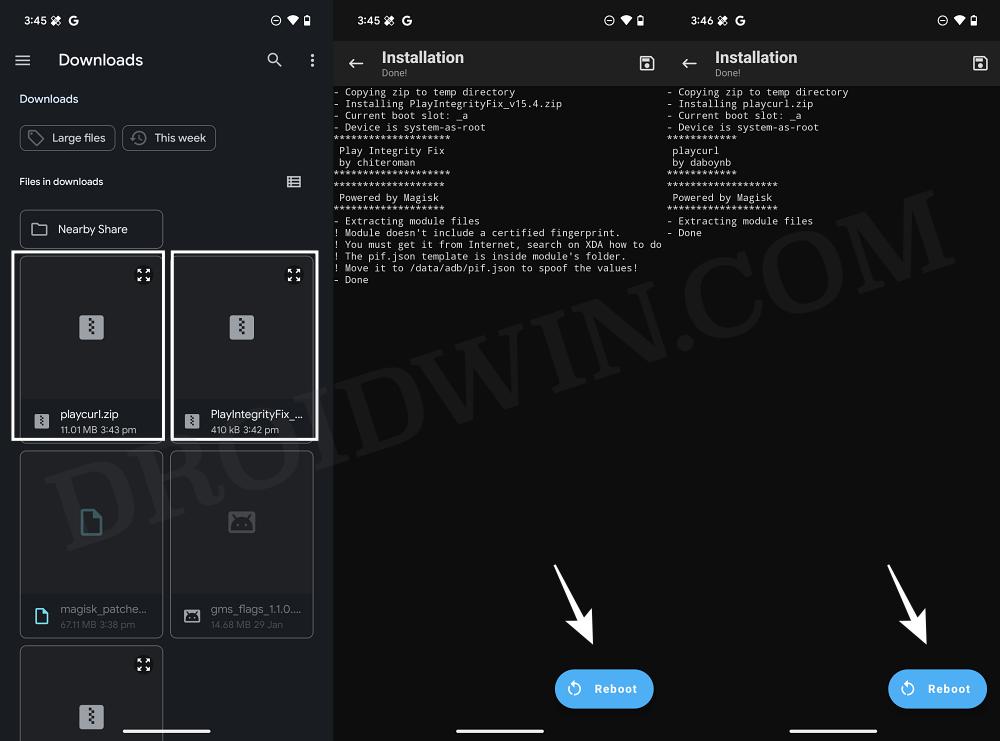
- The module will be flashed. Now flash the Play Integrity Fix module.
- Once done, restart your device and install the AutoPIF-Next app.
- Then go to Settings > Apps > All Apps > AutoPIF-Next > Notifications and enable all the notifications.
- Now launch AutoPIF-Next and you’ll get a Magisk prompt, tap on Grant.
- Likewise, you’ll also get a notification that the new pif.json is implemented.
- Once that happens, check if your device is passing the Play Integrity or not.
- If it isn’t, then once again open AutoPIF-Next and check out the result.
How to Check if my Device is passing Play Integrity Test
There are two different methods of checking if your device is passing the Play Integrity Test or not- via Play Store and using a third-party app. Let’s make you aware of both these approaches:
Via Play Store
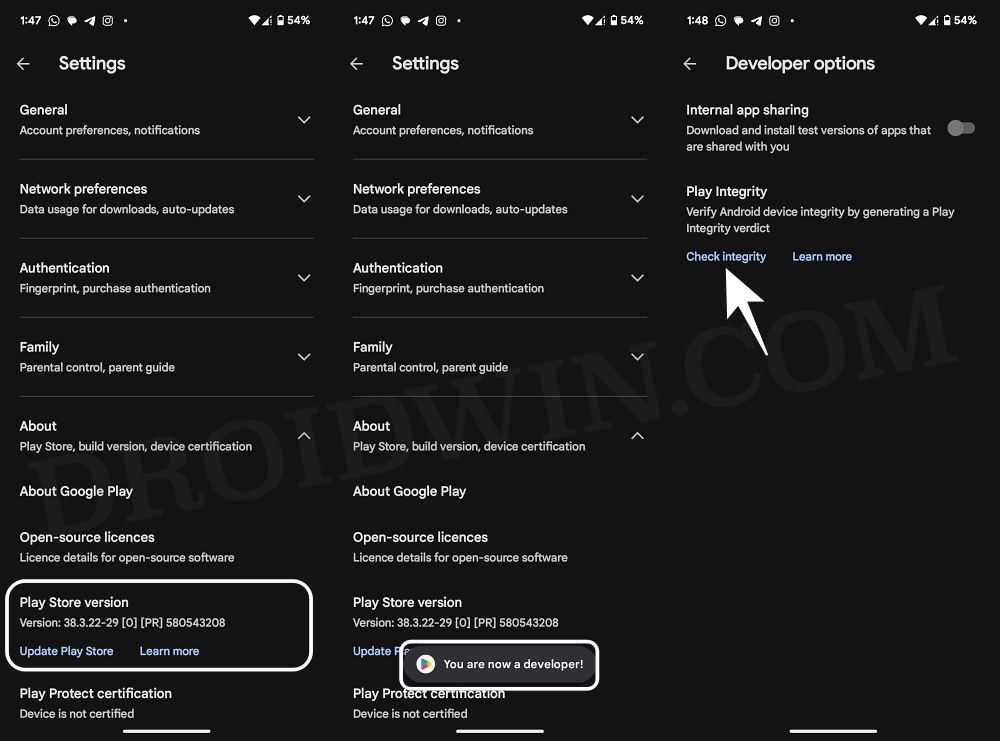
- Launch Play Store > tap on your profile at the top right > Settings > About.
- Now tap on Play Store version 8 times. This will enable Developer Options.
- Then go to Settings > General > Developer options > tap on Check integrity.

Using Third-Party Apps
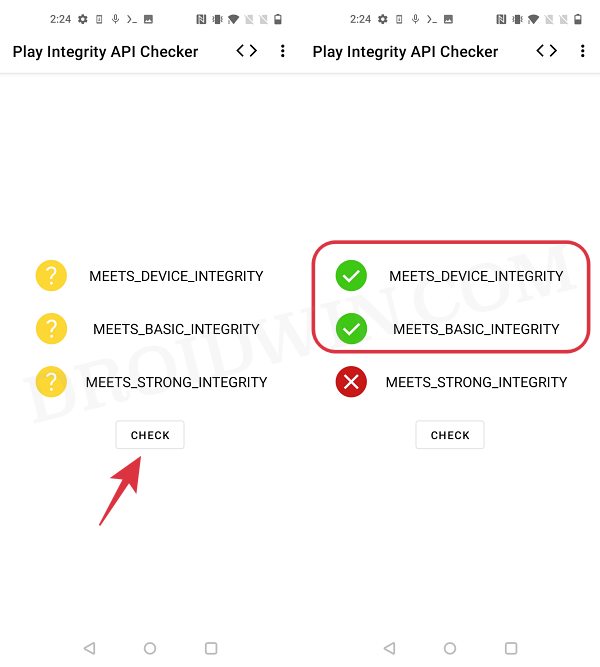
You could also get this job done via third-party apps like Play Integrity API Checker [which only checks for Play Integrity] and TB Checker [which would additionally check for traces of rooted apps present on your device].

Using Custom Fingerprint/Build.prop to Pass SafetyNet
if the aforementioned method didn’t spell out success, then it could be attributed to the fact that Google has patched that fingerprint/build.prop. In such cases, you will have to get hold of the fingerprint/build.prop from a less popular device+firmware version that hasn’t been used by many [a few Chinese phones out there in the market might checkmark this requirement].
Use Custom Fingerprint/Build.Prop to Pass Play Integrity Test
In this regard, there are three different methods of getting this job done- one click, automatic, and manual. Go through each of them once listed in the above guide and then try out the one that is in sync with your requirement.
My Device is Failing MEETS_STRONG_INTEGRITY
As mentioned before, as long as your device’s bootloader is unlocked, it will fail the MEETS_STRONG_INTEGRITY check. That is not a cause of any concern as you’ll still be able to use the banking apps without any issues. But if for some reason, you wish to pass this test, then your only course of action is to remove all modules, unroot your device, and then relock the bootloader.

My Device is Passing SafetyNet but I Cannot Use Banking Apps
If your device is passing SafetyNet and you still cannot use a banking or payment app, then this is happening because that app has already ditched this test and moved over to Play Integrity. So you’ll now have to pass the Play Integrity test to be able to use the app again.

That’s it. These were the steps to pass the “Meets Device Integrity” and Meets Basic Integrity” tests on your rooted device via the Play Integrity Fix module. If you have any queries concerning the aforementioned steps, do let us know in the comments. We will get back to you with a solution at the earliest.
How to Pass Play Integrity Test on Xiaomi EU ROM
Passing the Play Integrity Test on your Xiaomi EU ROM might be a tad bit different. So do refer to our below-linked guide [with video instructions] to get this job done:






DWP
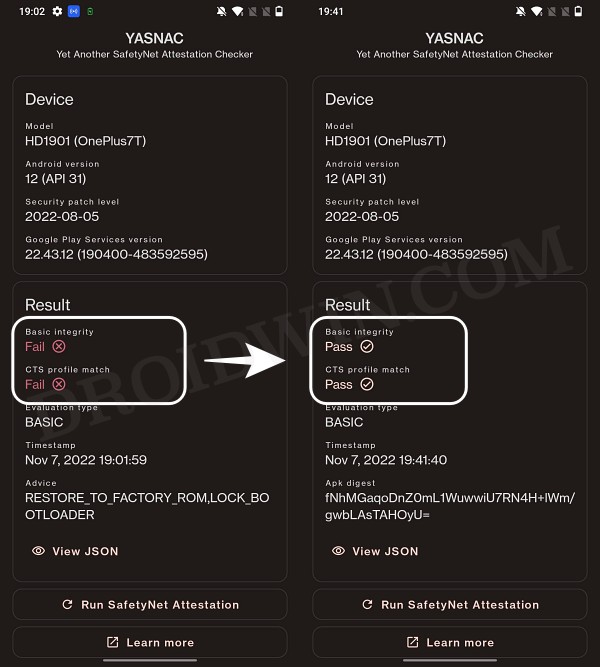
Hello and thanks for this helpful post… I am, however, still a little stuck… This is on a rooted, Android 9 LG V40 – if that makes any difference. I went the the process and the Integrity Checker app now shows it meets basic. But the other two still fail. If I understand the strong should NOT pass due to unlocked boot loader. But the Device should pass. The YASNAC app says it passes both Basic and CTS profile (where previously it pass neither). So I feel I am doing something wrong here but I am not sure what that might be.
My basic problem here is not really banking apps. But I have found that, increasingly, Play Store is showing that apps are “not compatible” when trying to install on a rooted device. This, for example, is the case with the Peacock TV app. And I really need to get around this. So any suggestions you might have are greatly appreciated. Thanks again!