In this guide, we will show you the steps to hide/spoof/fake the bootloader unlock status on your Android device. If you have rooted your device via Magisk, then you might be aware that numerous banking and payment apps will not work along the expected lines. This is because these apps perform a Play Integrity test in which your rooted device would be failing the Device and/or Basic Integrity tests.
Fortunately, you could pass that test using a custom build.prop fingerprint JSON file. But what about an unlocked bootloader? While most apps simply perform a root check, there are others out there that additionally perform a bootloader check as well. So if your device’s bootloader is unlocked [even if your device is not rooted], then it will straightaway refuse to function [such as the Uber Driver app].
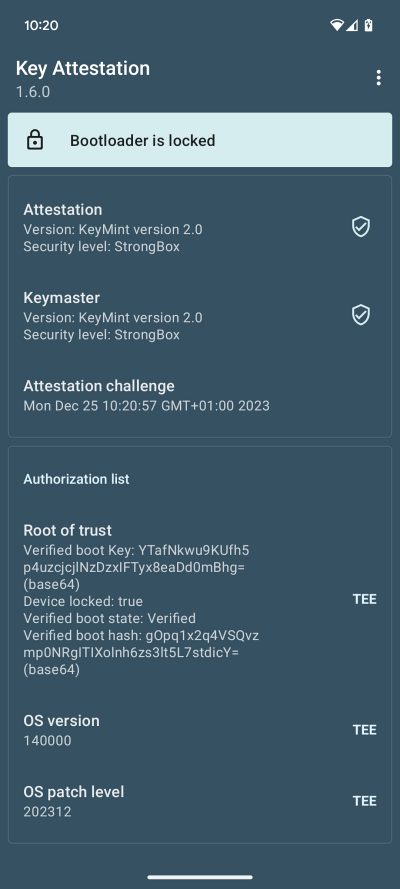
So to rectify this issue, you could either relock the bootloader [duh!] or keep the bootloader unlocked, but hide its true status and fake it to show that the bootloader is still locked on your device. Sounds interesting, right? So without further ado, let’s test it out right away.
How to Spoof/Fake/Hide Bootloader Unlock Status
First and foremost, you will still not be passing the Strong Integrity test. While this is not a case of any concern as none of the banking and payment apps checks for this, but still, we thought of making it apparent beforehand. The reason for the same is that even though you have “spoofed” your device bootloader status to be locked, in actuality, it is still unlocked.
Moreover, this module will not work with devices for which TEE is broken, like OnePlus [though there have been a few cases where it has worked with this OEM, so you could give it a try and check if it spells out success for you].
With that said, let’s now get straight to the point and hide the bootloader unlock status on your Android device right away. Droidwin and its members wouldn’t be held responsible in case of a thermonuclear war, your alarm doesn’t wake you up, or if anything happens to your device and data by performing the below steps.
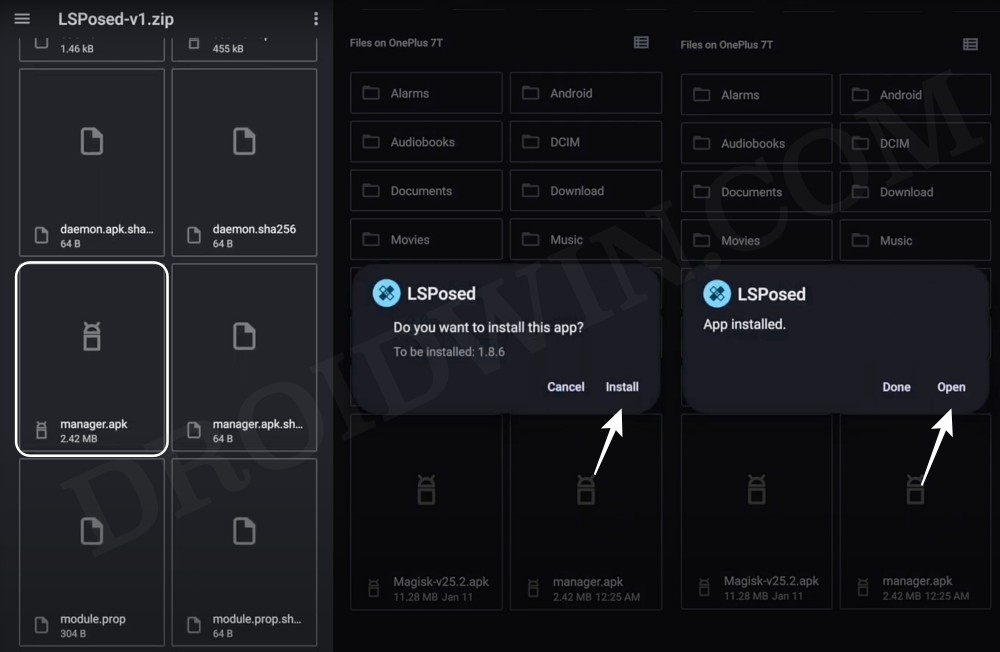
- Root your device via Magisk and then install LSPosed Framework.

- Now download and install Bootloader Spoofer from GitHub.
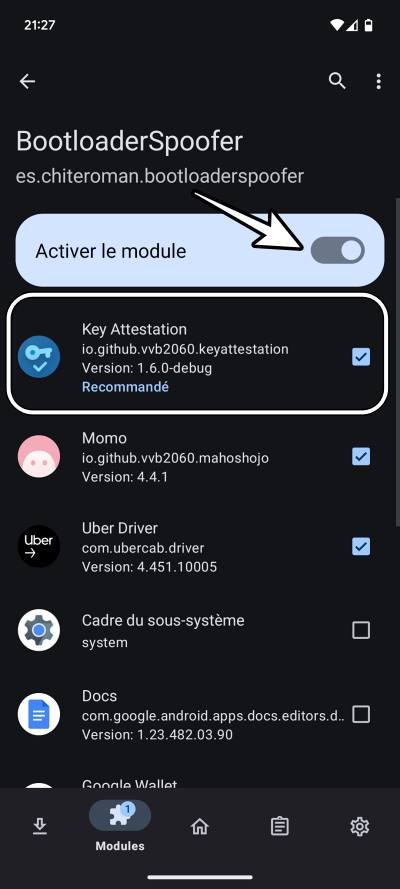
- Then launch LSPosed, go to Modules, and select Bootloader Spoofer.
- Now enable the toggle next to Activate Module and check Key Attestation.

- Then tick the apps that check for an unlocked bootloader.
- Once done, restart your device for the changes to take place.
- Now launch the app from which you have hidden bootloader unlock status and check the result.
- If it is still detecting the root, then delete its data, restart your device, and then re-verify the result.
That’s it. These were the steps to hide/spoof/fake the bootloader unlock status on your Android device. If you have any queries concerning the aforementioned steps, do let us know in the comments. We will get back to you with a solution at the earliest.
How to Pass Play Integrity Test
Since you have rooted your device to carry out the aforementioned task, your device will now be failing the Play Integrity test. Well, not an issue! Simply refer to our below guide to pass this test right away:
How to pass ‘Meets Device and Basic Integrity’ via Play Integrity Fix