In this guide, we will show you the steps to pass the SafetyNet on your rooted Google Pixel 6/Pro devices. The newest entry in the Pixel family has bought in quite a few goodies for general users. Along the same lines, it is proving to be quite an active player in custom development. The support that both these devices have received since their release is quite commendable, to say the least.
As of now, you could easily unlock the device’s bootloader and gain administrative access by rooting your device via Magisk. This will then allow you to flash a plethora of mods such as Magisk Modules, Xposed Frameworks, Substratum Themes, Viper4Android among others. However, this is just one side of the coin. Once you root your device, it will end up trigging the SafetyNet. As a result, banking and payment apps as well as games like Pokemon Go wouldn’t function on your device.
While bidding adieu to the games isn’t that much of a sacrifice, but the inability to use banking and payment apps is a major red flag for rooted users. Fortunately, there does exist a method through which you could pass the SafetyNet on your rooted Google Pixel 6/Pro device. And in this guide, we will help you with just that. So without further ado, let’s check it out.
Table of Contents
How to Pass SafetyNet in Rooted Pixel 6/Pro
Given below are two different methods to get this job done. The first method is the old and lengthier approach but initially, it was our only escape route. However, now there is a new and shorter approach available as well, which we have listed in Method 2 [recommended]. Both these methods should work across numerous Android devices [tested on Pixel 6/7 series and the OnePlus 7 series].
Likewise, it should work on both Android 12 and 13 [should also work on older Android versions, but I haven’t tested them myself]. So on that note, let’s get started. Droidwin and its members wouldn’t be held responsible in case of a thermonuclear war, your alarm doesn’t wake you up, or if anything happens to your device and data by performing the below steps.
METHOD 1: Pass SafetyNet using Magisk Hide Props Config [OLD]
This is the lengthier of the two methods and involves spoofing the device’s fingerprint to one of the older devices that followed Basic Attestation and were easier to bypass.
![]()
STEP 1: Install Riru Module
First off, you will have to install the Riru Module, which is a prerequisite for the SafetyNet Fix Module.
- Download the Riru Module from GitHub and transfer it to your device.
- Then launch the Magisk App and go to the Modules section.

- After that, tap on Install from Storage, select the module, and hit Install.
- Once done, tap on the Reboot button that appears at the bottom right.
STEP 2: Flash Universal SafetyNet Fix on Pixel 6/Pro
Next up, you will have to flash the latest version of the USNF (Universal SafetyNet Fix) module via Magisk. So refer to the below steps to try it out:
- To begin with, download the USNF module and transfer it to your device: safetynet-fix-v2.2.0. [Check for Latest Version]
- Then install the Magisk App onto your device. As of now, it is recommended to install the Canary build.
- Now launch the Magisk App and go to the Modules section.

- Then tap on Install from storage, navigate to the safetynet fix module and select it.
- The flashing shall now begin and would take a few seconds. Once done, reboot your device for the module to be active.
STEP 3: Enforce Deny List and Enable Zygisk
Deny List is the new name for Magisk Hide. For the unaware, it is the feature through which you could hide root from various installed apps onto your device. So let’s first enable this Deny List and then configure it according to the requirement.
- Launch the Magisk App onto your device
- Then tap on the Settings icon situated at the top right.
- Now enable the toggle next to Zygisk and Enforce Deny List.

- Now restart your device for the changes to take place. Then launch Magisk and make sure it says YES next to Zygisk.

STEP 4: Configure Deny List
Deny List is the new name for Magisk Hide. For the unaware, it is the feature through which you could hide root from various installed apps onto your device. So let’s first enable this Deny List and then configure it according to the requirement.
- Under the Magisk Settings menu, tap on Configure DenyList.
- Now, select the desired user apps in order to hide root from it [optional].

- After that, tap on the overflow icon situated at the top right and select Show System App.
- Now checkmark Google Play Protect Services, Google Play Services, Google Play Store. and Google Service Framework.

- NOTE: Upon restart, the Google Service Framework might get unchecked and Google Play Services might be missing from the DenyList. This is just a UI bug and nothing to worry about [they are still active in the backend].
STEP 5: Hide the Magisk App
Some apps not only check for the SafetyNet flag but also verify if the Magisk app is installed onto your device or not. Therefore, let’s disguise this app so that it re-installs itself with a different package name. Follow along.
- To begin with, launch the Magisk App on your device.
- Then tap on the gear icon situated at the top right to access its Settings menu.
- Then go to Hide the Magisk App option and let the feature do its job.

- Once done, it will ask whether you wish to have the app shortcut on the home screen.
- For ease of convenience, you may select Yes and then tap on the Add to Home Screen button.

STEP 6: Install MagiskHide Props Config
- Download MagiskHide Props Config from GitHub/XDA and transfer it to your device.
- Then launch the Magisk App onto your device.

- After that, tap on Install from Storage, select the Module, and hit Install.
- Once the installation is complete, hit the Reboot button situated at the bottom right.
STEP 7: Force Basic Attestation
We will now be starting with the implementation of the BASIC attestation on top of the hardware-based so that it becomes easier to bypass. Here’s how it could be done:
- First off, install any terminal emulator app on your device (such as the Termux app).
- Now launch it and type in the below command:
su -c props
- You will now get a Superuser Request, tap Grant.
- It shall now launch the MagiskHide Props Config within the terminal itself. Type in 2 [Force BASIC Key Attestation] and hit Enter.

- This shall take you to the Force BASIC Key Attestation page. By default, the value will be set to Nexus 5.
- While there is no particular value as such that would surely spell out success, but the one from Nexus 6P or Pixel 3A seems to be giving the best results.
- In this regard, I have used the Nexus 6P value on my rooted device running Android 12 and was able to pass the Safetynet, so let’s choose that one [Read FAQ at the end]. To do so, type in d [Yes, pick value from device list] and hit Enter.
- Then type in 7 [Google] and press Enter. After that, type 5 [Google Nexus 6P] and hit Enter.

- It will now ask you to confirm the selected value, type y [YES], and hit Enter.
- Finally, you will have to reboot the device. So type y [YES] and press Enter.

STEP 8: Delete Google Service Play Store Data
Next up, you will have to delete the Google Service and Play Store data. Here’s how it could be done:
- Head over to Settings > Apps > See All Apps and go to the Google Play Service app.
- Go to its Storage and Cache section and tap on Manage Space.

- Then tap on Clear All Data followed by OK in the confirmation dialog box.
- Once that is done, go to the Google Play Store app’s Storage and Cache section.

- After that, tap on Clear Storage followed by OK in the confirmation dialog box.
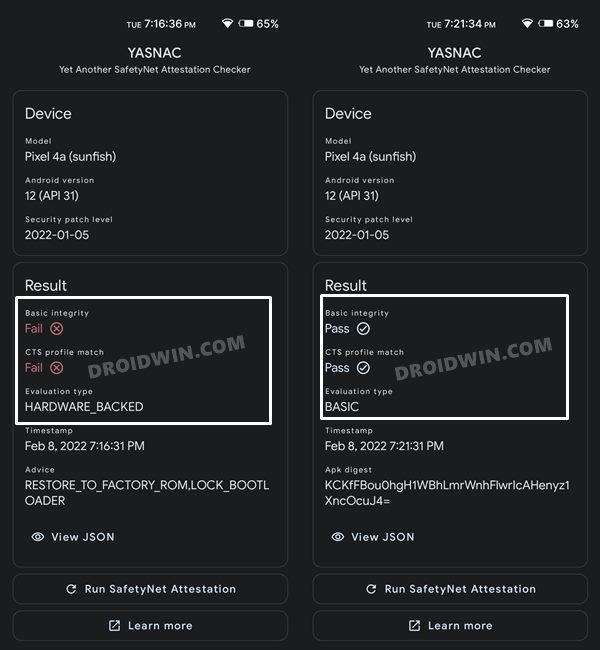
STEP 9: Check SafetyNet Result on Rooted Pixel 6/Pro
UPDATE 1: The latest update to the Magisk app has removed the option to check SafetyNet. So you will now have to take the help of a third-party app. As for this guide, we will be using the YASNAC – Yet Another SafetyNet Attestation Checker.
- So download YASNAC from the Play Store and install it onto your device.
- Then launch the app and tap on Run SafetyNet Attestation.

Before and After - You should now get the Pass result under both the basicIntegrity and ctsProfile sections.
The older method of checking Safetynet via Magisk is preserved below:
- Connect your device to the internet, launch the Magisk app, and tap on the Check Safetynet button.
- If this is the first time you are performing this check, then you will get Download Priopreitary Code pop-up, tap OK.

- As soon as the code is downloaded, the test will begin.
- Within a couple of seconds, you should now see the Pass message next to both the BasicIntegrityCTS Profile.
So with this, you have successfully passed the SafetyNet on your rooted Pixel 6/Pro device. And on that note, we round off this guide as well. All your queries are welcomed in the comments section below.
Update for Android 13
For my device running Android 13, I choose Pixel 3 device and selected Android 1o as the OS in STEP 2 above. So if you have any doubts, then it’s better to select that one as it has been tried and tested.
![]()
Attaching hereby the results of passing SafetyNet on rooted Android 13:
![]()
METHOD 2: Pass SafetyNet without Magisk Hide Props Config [NEW]
The shorter of the two methods, this doesn’t require you to spoof the device’s fingerprint or flash the Magisk Hide Props Config, all thanks to tweaks made by the developer of the Universal SafetyNet Fix Module. So on that note, let’s get started with the steps to pass Safetynet on your rooted Pixel 6/Pro.
![]()
STEP 1: Hide Magisk App
- Launch the Magisk App and tap on the settings icon situated at the top right.
- Then tap on Hide the Magisk App > Enable the toggle next to Allow apps from this source.

- Assign a new random name to this Magisk app and hit OK.
- It will now ask for a home-screen shortcut, tap OK [recommended].

STEP 2: Enable Systemless Hosts
- Launch the Magisk App and tap on the settings icon situated at the top right.
- Then tap on Systemless hosts.
- Now go to the Modules section and verify that it has been added.

STEP 3: Enable Zygisk
- Launch the Magisk App and tap on the settings icon situated at the top right.
- Then enable the toggle next to Zygisk and restart your phone.
- Now launch Magisk and make sure that it says YES next to Zygisk.

STEP 4: Configure Denylist
Denylist is the new name for the traditional Magisk hide. You could use this functionality to hide root from the desired apps, apart from the three compulsory apps listed below.
- Launch the Magisk App and tap on the settings icon situated at the top right.
- Then enable the toggle next to Enforce Denylist. Now tap on Configure Denylist.

- Then expand the following apps and checkmark all its services
Google Play Service Google Play Store Google Service Framework Google Play Protect Service [if present]

- After that, do the same for the banking/payment app of your choice.
- NOTE: Upon restart, the Google Service Framework might get unchecked and Google Play Services might be missing from the DenyList. This is just a UI bug and nothing to worry about [as they are still active in the backend].
STEP 5: Flash Universal SafetyNet Fix Module
- Download the new Universal SafetyNet Fix module from below:
safetynet-fix-v2.3.1.zip [Source: GitHub]
- Then launch Magisk, go to the Modules section, and tap on Install from Storage.

- Navigate to the downloaded safetynet module and select it.
- It will now be flashed. Once done, hit Reboot.
STEP 6: Delete Data
You will now have to delete the app data of all the apps from which you have hidden root. These include the compulsory Google apps and the desired apps of your choice.
- Head over to Settings > Apps and select Google Play Service.
- Then go to its Storage section and tap on Manage Space > Clear all data.
- After that, delete the data of Google Play Store and Google Play Protect Service [if present].
- Then tap on the overflow icon situated at the top right and select Show System.

- This will bring up the system apps. Select Google Service Framework and delete its data.
- Finally, delete the data of the banking/payment apps from which you have hidden root. Once done, restart your device [compulsory].
STEP 7: Check SafetyNet Test Results
- Download and install the YASNAC app from Play Store.
- Then launch it and tap on Run SafetyNet Attestation.
- You should now get Pass under both Basic Integrity and CTS Profile Match.

That’s it. these were the steps to pass SafetyNet on your rooted Pixel 6/Pro. If you have any queries concerning the aforementioned steps, do let us know in the comments. We will get back to you with a solution at the earliest.